티스토리 뷰
▶ passphrase : hello 입력
[kildong@control ~]$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kildong/.ssh/id_rsa):
Created directory '/home/kildong/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Passphrases do not match. Try again.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kildong/.ssh/id_rsa.
Your public key has been saved in /home/kildong/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:T45kiJeeExkiWYYtJjLatmVfIFGrmdM5dcD2W/3wXfk kildong@control.example.com
The key's randomart image is:
+---[RSA 2048]----+
| o+o... |
|+ ++o ..o. |
|o=o...oo... . .|
|. o.oB B... . o..|
| . +*.X.S .o ++|
| . +.* =. E|
| + . o |
| . |
| |
+----[SHA256]-----+
▶개인키는 복사 안된다 ( 타인 ) >> 권한 확인
[kildong@control ~]$ cd .ssh
[kildong@control .ssh]$ ll
total 8
-rw-------. 1 kildong kildong 1766 Feb 7 01:12 id_rsa
## 개인키
-rw-r--r--. 1 kildong kildong 409 Feb 7 01:12 id_rsa.pub
## 공개키
▶ftp 로는 업로드 안한다
>> scp / sftp 로 id/pw를 모르도록 전달
>> ssh는 rsa 인증방식이므로 거의 못깬다
[vagrant@node1 ~]$ sudo cat /etc/ssh/sshd_config |grep authorized
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2>> 상대 경로로 /home 디렉터리 밑에 .ssh/authorized_keys 에서 확인한다
# authorized_keys2 인 경우도 있으므로 확인하고 작업
>> 미리 kdhong에 .ssh 만들어두기
[kdhong@node1 ~]$ mkdir .ssh[kildong@control .ssh]$ sftp kdhong@192.168.110.20
The authenticity of host '192.168.110.20 (192.168.110.20)' can't be established.
ECDSA key fingerprint is SHA256:dJUzL1q0e45rkPCjG9Gvii2kqv9JNMsSSlSUzpoh1Ts.
ECDSA key fingerprint is MD5:90:fd:e8:8b:48:a2:74:2e:10:33:43:2f:53:1c:4a:ed.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.110.20' (ECDSA) to the list of known hosts.
kdhong@192.168.110.20's password:
Connected to 192.168.110.20.
sftp> helpsftp> lcd /home/kildong/.ssh/
sftp> !pwd
/home/kildong/.ssh
sftp> pwd
Remote working directory: /home/kdhong
sftp> cd .ssh
sftp> !ls
id_rsa id_rsa.pub known_hosts
sftp> put id_rsa.pub /home/kdhong/.ssh/id_rsa.pub
Uploading id_rsa.pub to /home/kdhong/.ssh/id_rsa.pub
id_rsa.pub 100% 409 1.1MB/s 00:00
sftp> !ls
id_rsa id_rsa.pub known_hosts
sftp> exit
>> chmod 700 .ssh 로 변경해야 한다 ( 보안 )
## ssh 서버가 권한이 755로 잘못되어 있으면
## 보안상 문제가 있다고 판단하여 password 를 요구한다
[kdhong@node1 .ssh]$ ls
id_rsa.pub
[kdhong@node1 .ssh]$ mv id_rsa.pub authorized_keys
[kdhong@node1 .ssh]$ ls
authorized_keys
[kdhong@node1 .ssh]$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCZ1k9m2EXw
/4HjVAE9FIfBC25YEKFFvMqKOakgGdSqKo0L02XalQVUZDAnqyZ1
J23IgkRF7A5nA9DlodKxqZVAimwyma1xpL03TPM7KwPx6TNt16YrWY5H
8j1U4lYLfp0cLDWJOcf+N5JMjApocccwXXdasJcipapAGz+q8k0Y/1C+u
eH0e8EthvE5Te3RJmj5S2xIObRR7XiuWR9NztHhKta0eTeGZwkefFq38sk
NUquZGYgHJbzjxpvmGecSSXpsyFytKMqR4TQcuSUh+/OUvkcKvAPjOCSOH
TEkrNSc38CLu8p7HIuJFHRh9fjBwoP1+
KBQHIocjXx0dGyQvz8/ kildong@control.example.com
[kdhong@node1 .ssh]$ cd
[kdhong@node1 ~]$ chmod 700 .ssh
>> passphrase 로 password가 아닌 입장 ( hello )
[kildong@control .ssh]$ ssh kdhong@192.168.110.20
Enter passphrase for key '/home/kildong/.ssh/id_rsa':
Last login: Wed Feb 7 01:18:30 2024 from 192.168.110.1
[kdhong@node1 ~]$
● 다른 방식 ( 더 쉽다 )
[kdhong@node1 ~]$ rm -rf .ssh
[kdhong@node1 ~]$ ll
total 0
[kdhong@node1 ~]$ ll -all
total 12
drwx------. 2 kdhong kdhong 62 Feb 7 01:44 .
drwxr-xr-x. 5 root root 49 Feb 7 01:05 ..
-rw-r--r--. 1 kdhong kdhong 18 Apr 1 2020 .bash_logout
-rw-r--r--. 1 kdhong kdhong 193 Apr 1 2020 .bash_profile
-rw-r--r--. 1 kdhong kdhong 231 Apr 1 2020 .bashrc
>> default 경로이므로 생략 가능
[kildong@control .ssh]$ ssh-copy-id .ssh/id_rsa.pub kdhong@192.168.110.20
>> .ssh 디렉터리 없으면 만들어주고 authorized.keys 파일로 올려준다
## 권한까지 해결해 준다
[kildong@control .ssh]$ ssh-copy-id kdhong@192.168.110.20
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/kildong/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
kdhong@192.168.110.20's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'kdhong@192.168.110.20'"
and check to make sure that only the key(s) you wanted were added.[kdhong@node1 ~]$ ll -a
total 16
drwx------. 3 kdhong kdhong 95 Feb 7 01:46 .
drwxr-xr-x. 5 root root 49 Feb 7 01:05 ..
-rw-------. 1 kdhong kdhong 5 Feb 7 01:44 .bash_history
-rw-r--r--. 1 kdhong kdhong 18 Apr 1 2020 .bash_logout
-rw-r--r--. 1 kdhong kdhong 193 Apr 1 2020 .bash_profile
-rw-r--r--. 1 kdhong kdhong 231 Apr 1 2020 .bashrc
drwx------. 2 kdhong kdhong 29 Feb 7 01:46 .ssh
[kdhong@node1 ~]$ cd .ssh
[kdhong@node1 .ssh]$ ll
total 4
-rw-------. 1 kdhong kdhong 409 Feb 7 01:46 authorized_keys
control node1
kildong> ssh kdhong@node1
/home/kildong/.ssh/known_hosts
node1 암호화된 핑거프린터
sshd <<<<
sshd 가 문제가 없는지 판단
sshd 가 /home/kdhong/.ssh/authorized_keys 가 있는지 찾아본다
난수 8392912
해독하여 passphrase 있으면 물어본다
▶ 암호화
GNU 로 개발하는 사람들은 소스만큼은 공개해야 한다
>> GPG [ GNU Privacy Guard ]
>> PGP 가 나온 이후로 국가에서 개인 mail을 볼 수 없게되었다
[ 메일을 암호화 시키기 위한 목적으로 개발 ]
- GPG 는 PGP 를 완전히 대신할수 있음 ( 라이센스만 차이난다 )
- GPL 을 따르며 누구나 제약없이 사용 가능
- 공개키 방식의 암호화 기법을 사용
- 키서버를 지원
>> 공개키를 공개가능
gpg --version : 버전확인
키생성(공개키 및 개인키)
gpg --gen-key
[lee@server1 ~]$ gpg --gen-key
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection?
* RSA
- 서명과 암호화
* Elgamal
- 서명과 암호화
* DSA
- 전자서명을 통해 인증, 무결성, 부인방지 제공
기밀성 유지에는 사용되지 않는다.
* rngd - Check and feed random data from hardware device to kernel random
device
gpg --list-keys / gpg --list-public-keys
- 공개키 목록 출력
gpg --list-secret-keys
- 개인키 목록 출력
- gpg 공개키 추출
public key 를 아스키 파일로 생성
gpg --export -a --output mypubkey.gpg ;
옵션:
--export : keyring 에서 공개키 추출
--armor(== -a) : ascii
public key 를 바이너리 파일로 생성
gpg --export --output mypubkey2.gpg ;
상대방의 공개키 등록(public keyring)
gpg --import younghee_pubkey.gpg
메세지를 암호화 - 이메일 주소는 해독할 사람의 메일주소
$ gpg -ear kildong@naver.com test.txt
e: encrypt
a: ascii
r: 암화화에 사용할 사용자 아이디 또는 이메일
s: 서명
메시지 복호화는 gpg -d 암호화된파일명.
메시지에 서명(서명은 자신의 개인키로 한다)
gpg -sar kildong@naver.com test.txt
메시지를 암호화 + 서명
gpg -sea test.txt
* 메시지 서명 검증(서명 검증은 상대방의 공개키로 한다)
gpg --verify s.txt.asc
* 상대방의 공개키에 서명을 하지 않으면
상대방의 서명을 검증할때 아래와 같은 경고가 출력된다.
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
* 상대방의 공개키에 서명(상대방의 공개키를 확실하게 신뢰하는 경우에만 서명한다)
- gpg --sign-key younghee@naver.com
◎ [ 공개키로 메일을 암호화 시킨다 ]
[kildong@control ~]$ cat to_younghee.txt
하나은행 : 123-1234-1234
예금주 : 홍길동
연락처 : 010-1234-1234
* 100 만원을 입금해주세요.
>> /home/kildong/.gnupg/secring.gpg 공개키가 이곳에 저장되므로 백업을 해둬야 한다
>> /home/kildong/.gnupg/pubring.gpg 공개키와 개인키는 세트이므로 둘 다 백업
[kildong@control ~]$ gpg --gen-key
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
gpg: directory `/home/kildong/.gnupg' created
gpg: new configuration file `/home/kildong/.gnupg/gpg.conf' created
gpg: WARNING: options in `/home/kildong/.gnupg/gpg.conf' are not yet active during this run
gpg: keyring `/home/kildong/.gnupg/secring.gpg' created
gpg: keyring `/home/kildong/.gnupg/pubring.gpg' created
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(1) > 서명 RSA 암호 RSA
(2) > 서명 DSA 암호 Elgamal
>>>> 서명 암호 둘다 쓸거면 1 아님 2Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
>> 너무 크면 부하 준다Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 2
Key expires at Fri 09 Feb 2024 02:11:44 AM UTC
Is this correct? (y/N) y
>> 2일동안 사용가능한 기간 설정GnuPG needs to construct a user ID to identify your key.
Real name: hong kildong
Email address: kildong@naver.com
Comment: nnononono
You selected this USER-ID:
"hong kildong (nnononono) <kildong@naver.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? c
Comment: cloud engineer
You selected this USER-ID:
"hong kildong (cloud engineer) <kildong@naver.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? o
>> 메일 주소는 정확하게 넣어야 한다
>>> 개인키 암호
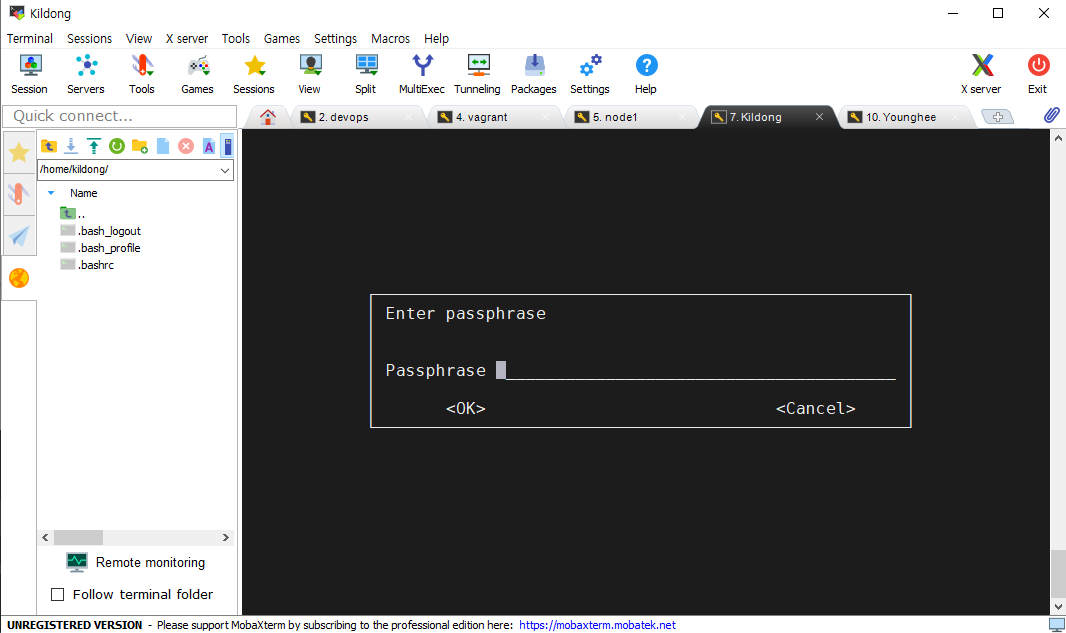



You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
>>> 엔트로피가 부족하여 난수가 생성이 부족하므로 rng-tools 설치한다
>> rng : Random Number Generator
[vagrant@control ~]$ sudo yum list rng-tools
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirror.elice.io
* centos-ansible-29: mirror.elice.io
* extras: mirror.elice.io
* updates: mirror.elice.io
Available Packages
rng-tools.x86_64 6.3.1-5.el7 base
[vagrant@control ~]$ sudo systemctl start rngd[vagrant@control ~]$ sudo rngd --rng-device=/dev/hwrng
Initalizing available sources
Failed to init entropy source 0: Hardware RNG Device
Enabling RDRAND rng support
Initalizing entropy source Intel RDRAND Instruction RNG
Enabling JITTER rng support
Initalizing entropy source JITTER Entropy generator
>>> 엔트로피 부족 문제 해결 완료
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: /home/kildong/.gnupg/trustdb.gpg: trustdb created
gpg: key 9C48786B marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
gpg: next trustdb check due at 2024-02-09
pub 2048R/9C48786B 2024-02-07 [expires: 2024-02-09]
Key fingerprint = 981B D63E 14DD 7D55 0E87 4859 E7E8 2F89 9C48 786B
uid hong kildong (cloud engineer) <kildong@naver.com>
sub 2048R/A906F09E 2024-02-07 [expires: 2024-02-09]
>> 잘 만들어져 있는지 확인
>> pub 공개키
>> 9C48786B >> fingerprint
[kildong@control ~]$ gpg --list-keys
/home/kildong/.gnupg/pubring.gpg
--------------------------------
pub 2048R/9C48786B 2024-02-07 [expires: 2024-02-09]
uid hong kildong (cloud engineer) <kildong@naver.com>
sub 2048R/A906F09E 2024-02-07 [expires: 2024-02-09][kildong@control ~]$ gpg --list-secret-keys
/home/kildong/.gnupg/secring.gpg
--------------------------------
sec 2048R/9C48786B 2024-02-07 [expires: 2024-02-09]
uid hong kildong (cloud engineer) <kildong@naver.com>
ssb 2048R/A906F09E 2024-02-07
메세지를 받을 사람이 공개키를 줘야한다........
지금 반대로 했다......
길동이 보내고 영희가 받아야하는데
길동이 공개키를 만들었다.
>> 길동의 공개키 추출
[kildong@control ~]$ gpg --export -a --output kildong_pub.gpg
[kildong@control ~]$ ll -a
total 24
drwx------. 4 kildong kildong 150 Feb 7 02:56 .
drwxr-xr-x. 6 root root 66 Feb 7 02:00 ..
-rw-r--r--. 1 kildong kildong 18 Apr 1 2020 .bash_logout
-rw-r--r--. 1 kildong kildong 193 Apr 1 2020 .bash_profile
-rw-r--r--. 1 kildong kildong 231 Apr 1 2020 .bashrc
drwx------. 3 kildong kildong 162 Feb 7 02:46 .gnupg
-rw-rw-r--. 1 kildong kildong 1760 Feb 7 02:56 kildong_pub.gpg
drwx------. 2 kildong kildong 57 Feb 7 01:46 .ssh
-rw-rw-r--. 1 kildong kildong 114 Feb 7 02:52 to_younghee.txt
-rw-------. 1 kildong kildong 938 Feb 7 02:52 .viminfo
[kildong@control ~]$ cat kildong_pub.gpg
>> 영희가 가져온다
[younghee@control ~]$ cp /tmp/kildong_pub.gpg .
[younghee@control ~]$ ll
total 8
-rw-rw-r--. 1 younghee younghee 1760 Feb 7 02:57 kildong_pub.gpg
-rw-rw-r--. 1 younghee younghee 99 Feb 7 02:54 to_kildong.txt
>>> 등록
[younghee@control ~]$ gpg --import kildong_pub.gpg
gpg: directory `/home/younghee/.gnupg' created
gpg: new configuration file `/home/younghee/.gnupg/gpg.conf' created
gpg: WARNING: options in `/home/younghee/.gnupg/gpg.conf' are not yet active during this run
gpg: keyring `/home/younghee/.gnupg/secring.gpg' created
gpg: keyring `/home/younghee/.gnupg/pubring.gpg' created
gpg: /home/younghee/.gnupg/trustdb.gpg: trustdb created
gpg: key 9C48786B: public key "hong kildong (cloud engineer) <kildong@naver.com>" imported
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
>>> 확인
[younghee@control ~]$ gpg --list-keys
/home/younghee/.gnupg/pubring.gpg
---------------------------------
pub 2048R/9C48786B 2024-02-07 [expires: 2024-02-09]
uid hong kildong (cloud engineer) <kildong@naver.com>
sub 2048R/A906F09E 2024-02-07 [expires: 2024-02-09]
>> 신뢰하는가를 묻는다
>> 이메일 주소는 공개키에 등록할 때 썼던 길동의 이메일 적는다
[younghee@control ~]$ gpg -e -a -r kildong@naver.com to_kildong.txt
gpg: A906F09E: There is no assurance this key belongs to the named user
pub 2048R/A906F09E 2024-02-07 hong kildong (cloud engineer) <kildong@naver.com>
Primary key fingerprint: 981B D63E 14DD 7D55 0E87 4859 E7E8 2F89 9C48 786B
Subkey fingerprint: A400 36F8 D35F 5675 7C98 5B3B BAAB D7A5 A906 F09E
It is NOT certain that the key belongs to the person named
in the user ID. If you *really* know what you are doing,
you may answer the next question with yes.
Use this key anyway? (y/N) y
>> 암호화 완료
[younghee@control ~]$ ll
total 12
-rw-rw-r--. 1 younghee younghee 1760 Feb 7 02:57 kildong_pub.gpg
-rw-rw-r--. 1 younghee younghee 99 Feb 7 02:54 to_kildong.txt
-rw-rw-r--. 1 younghee younghee 690 Feb 7 03:02 to_kildong.txt.asc
[younghee@control ~]$ cp to_kildong.txt.asc /tmp
>> 길동이 복호화
[kildong@control ~]$ gpg -d /tmp/to_kildong.txt.asc
You need a passphrase to unlock the secret key for
user: "hong kildong (cloud engineer) <kildong@naver.com>"
2048-bit RSA key, ID A906F09E, created 2024-02-07 (main key ID 9C48786B)
gpg: encrypted with 2048-bit RSA key, ID A906F09E, created 2024-02-07
"hong kildong (cloud engineer) <kildong@naver.com>"
하나은행 : 123-1111-1111
예금주 : 김영희
번호 : 010-1234-1234
100만원 입금 바람
▶ GPG Signature
gpg signature
- sign 하기전에 메시지 내용은 압축된다.
$ gpg [ --output messages.sig] --sign messages
=> binary 형태로 파일생성
* output 옵션을 생략하면 생성되는 디폴트 파일명은 파일명은 messages.asc
$ gpg [ --output messages.sig] --sign -a messages
=> ascii 형태로 파일생성
* output 옵션을 생략하면 생성되는 디폴트 파일명은 파일명은 messages.asc
$ gpg [--output messages] --decrypt messages.sig
압축을 풀기 어려운 환경에서 메시지를 수신해야 한다면
압축을 하지 않아야 한다.
메시지 내용을 압축을 하지 않고 sign 을 하려면
$ gpg [--output messages.sig] --clearsign messages
* gpg --compress-algo none 은 압축을 하지 않지만 메시지를
알수 없는 형태로 저장한다
* signature 검증
gpg --verify 파일명
* 서명된 메시지가 암호화가 된것이라면 복호화를 해야 서명을 검증할수 있다.
gpg -s -s -e id@google.com messages.txt => messages.txt.asc 파일에 저장
메일주소는 공개키 소유자의 메일주소
=>
gpg --veryfy messages.txt.asc => 서명검증안됨
gpg -d messages.txt.asc => 서명검증가능
------------------------------------------------------------------------
* gpg key 삭제
gpg --delete-key userid[kildong@control ~]$ gpg --sign -a to_younghee.txt
You need a passphrase to unlock the secret key for
user: "hong kildong (cloud engineer) <kildong@naver.com>"
2048-bit RSA key, ID 9C48786B, created 2024-02-07
[kildong@control ~]$ ll
total 16
-rw-rw-r--. 1 kildong kildong 1760 Feb 7 02:56 kildong_pub.gpg
-rw-rw-r--. 1 kildong kildong 114 Feb 7 02:52 to_younghee.txt
-rw-rw-r--. 1 kildong kildong 690 Feb 7 03:50 to_younghee.txt.asc
-rw-rw-r--. 1 kildong kildong 439 Feb 7 03:49 to_younghee.txt.gpg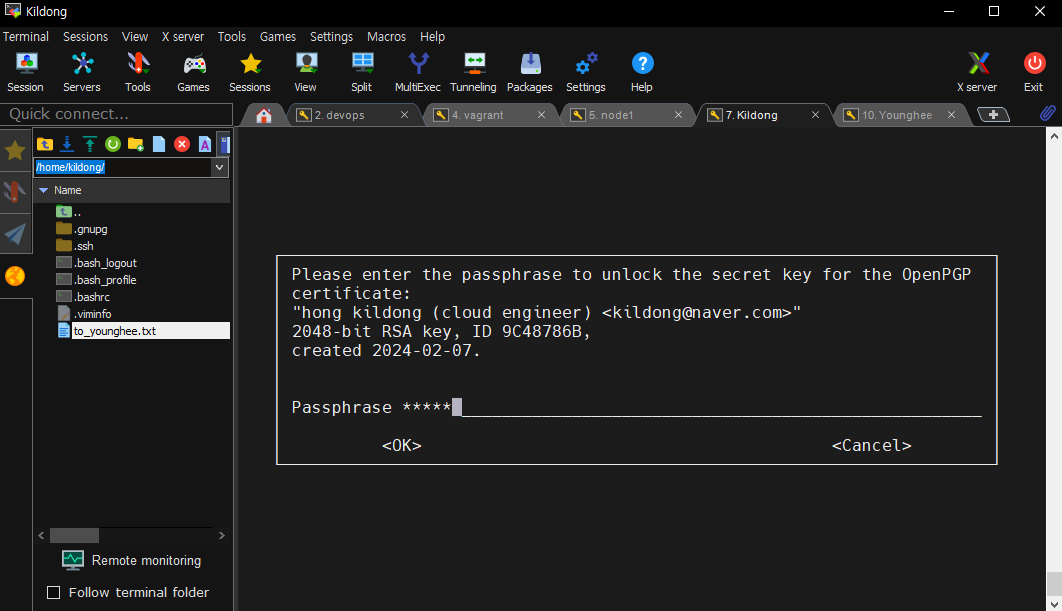
[kildong@control ~]$ cp to_younghee.txt.asc /tmp/[younghee@control ~]$ cp /tmp/to_younghee.txt.asc .
[younghee@control ~]$ ll
total 16
-rw-rw-r--. 1 younghee younghee 1760 Feb 7 02:57 kildong_pub.gpg
-rw-rw-r--. 1 younghee younghee 99 Feb 7 02:54 to_kildong.txt
-rw-rw-r--. 1 younghee younghee 690 Feb 7 03:02 to_kildong.txt.asc
-rw-rw-r--. 1 younghee younghee 690 Feb 7 03:51 to_younghee.txt.asc[younghee@control ~]$ cp /tmp/to_younghee.txt.asc .
[younghee@control ~]$ ll
total 16
-rw-rw-r--. 1 younghee younghee 1760 Feb 7 02:57 kildong_pub.gpg
-rw-rw-r--. 1 younghee younghee 99 Feb 7 02:54 to_kildong.txt
-rw-rw-r--. 1 younghee younghee 690 Feb 7 03:02 to_kildong.txt.asc
-rw-rw-r--. 1 younghee younghee 690 Feb 7 03:51 to_younghee.txt.asc
[younghee@control ~]$ gpg --list-keys
/home/younghee/.gnupg/pubring.gpg
---------------------------------
pub 2048R/9C48786B 2024-02-07 [expires: 2024-02-09]
uid hong kildong (cloud engineer) <kildong@naver.com>
sub 2048R/A906F09E 2024-02-07 [expires: 2024-02-09]
>> 검증부터 해본다
>> Good signature 이 뜨면 kildong이 맞다 라는 뜻
[younghee@control ~]$ gpg --verify to_younghee.txt.asc
gpg: Signature made Wed 07 Feb 2024 03:50:08 AM UTC using RSA key ID 9C48786B
gpg: Good signature from "hong kildong (cloud engineer) <kildong@naver.com>"
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 981B D63E 14DD 7D55 0E87 4859 E7E8 2F89 9C48 786B
>> 영희의 gpg 공개키 생성
[younghee@control ~]$ gpg --list-key
/home/younghee/.gnupg/pubring.gpg
---------------------------------
pub 2048R/9C48786B 2024-02-07 [expires: 2024-02-09]
uid hong kildong (cloud engineer) <kildong@naver.com>
sub 2048R/A906F09E 2024-02-07 [expires: 2024-02-09]
pub 2048R/2D16EF06 2024-02-07 [expires: 2024-02-09]
uid kim younghee (yh) <younghee@naver.com>
sub 2048R/EB8A3B32 2024-02-07 [expires: 2024-02-09]
>> kildong의 공개키에 영희가 신뢰하도록 서명한다
[younghee@control ~]$ gpg --sign-key kildong@naver.com
pub 2048R/9C48786B created: 2024-02-07 expires: 2024-02-09 usage: SC
trust: unknown validity: unknown
sub 2048R/A906F09E created: 2024-02-07 expires: 2024-02-09 usage: E
[ unknown] (1). hong kildong (cloud engineer) <kildong@naver.com>
pub 2048R/9C48786B created: 2024-02-07 expires: 2024-02-09 usage: SC
trust: unknown validity: unknown
Primary key fingerprint: 981B D63E 14DD 7D55 0E87 4859 E7E8 2F89 9C48 786B
hong kildong (cloud engineer) <kildong@naver.com>
This key is due to expire on 2024-02-09.
Are you sure that you want to sign this key with your
key "kim younghee (yh) <younghee@naver.com>" (2D16EF06)
Really sign? (y/N) y
>> 아까와 다르게 warning이 뜨지 않는다
[younghee@control ~]$ gpg --verify to_younghee.txt.asc
gpg: Signature made Wed 07 Feb 2024 03:50:08 AM UTC using RSA key ID 9C48786B
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 1 signed: 1 trust: 0-, 0q, 0n, 0m, 0f, 1u
gpg: depth: 1 valid: 1 signed: 0 trust: 1-, 0q, 0n, 0m, 0f, 0u
gpg: next trustdb check due at 2024-02-09
gpg: Good signature from "hong kildong (cloud engineer) <kildong@naver.com>"[younghee@control ~]$ gpg -d to_younghee.txt.asc
하나은행 : 123-1234-1234
예금주 : 홍길동
연락처 : 010-1234-1234
* 100 만원을 입금해주세요.
gpg: Signature made Wed 07 Feb 2024 03:50:08 AM UTC using RSA key ID 9C48786B
gpg: Good signature from "hong kildong (cloud engineer) <kildong@naver.com>"
| 인증서 : 서명이 되어 있는 공개키 | |
| 공인인증서 | 셀프인증서 |
| 공인된 기관에서 서명한 공개키 | 인증서를 만든 곳에서 직접 서명 |
| root CA 하고 관련된 기관 | 공인기관이 아니다 |
♠ 참조 ♠ http://gnupg.org
The GNU Privacy Guard
GnuPG versions 2.4.2, 2.4.3, and 2.2.42 had a regression in the default way to create smartcard keys. If you created a key with the –edit-key command using one of these versions, please head over to our security advisory: https://gnupg.org/blog/20240125-
gnupg.org
'Ansible' 카테고리의 다른 글
| yaml syntax (0) | 2024.02.07 |
|---|---|
| Ansible 의 기본 동작 (0) | 2024.02.07 |
| Ansible 시작 [ 공개키 / 개인키 ] (0) | 2024.02.06 |
| 직접 Vagrant file 만들기 (0) | 2024.02.06 |
| Ansible VM 기본 설정 (0) | 2024.02.06 |
